Threats and Concerns Before the Web
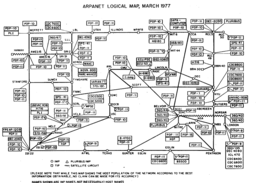
Before the open web, the evolving Internet was a relatively friendly and benign environment for its participants. Its end-to-end design principle, described in an influential 1981 conference paper by Saltzer, Reed, and Clark, encouraged its early users to build emerging services in ways that avoided specific dependencies on how and where their data was transmitted. Nonetheless, there was still concern about threats, whether from pranks or wiretappers.
What were the threats and concerns?
Wiretapping
Even in the early days of networking, data transmitted between mutually friendly sites needed to traverse
complex and unpredictable sets of routers and communications lines. While there was some interest in end-to-end encryption
of potentially sensitive data, implementation was limited.
Unauthorized Access to Services and Data
Even in the early Internet's collaborative environment, it was important to identify and distinguish
users, so that data and costly processing resources could be protected and conserved. While many data objects were
published for general access via anonymous File Transfer Protocol (FTP), access to others required registration with
individual usernames and passwords.
PC viruses
Before widespread use of networks, viruses were the primary security concern for
most PC users. Virus infections spread from the early days of PCs, initially accompanying programs
shared on floppy disks and subsequently carried via communications facilities.
Morris Worm
The Morris Worm (1988) was the
first publicized example of a worm spreading via the Internet, and led to the
first conviction under the US Computer Fraud and Abuse Act. It exploited vulnerabilities present in
thousands of connected Unix systems, consuming their processing resources.
 Information Security History: A Virtual Overview
Information Security History: A Virtual Overview