Security Techniques Before the Web
Many of the fundamental security techniques that are still used today were first developed in the pre-Web era. New cryptographic algorithms became available, and pilot Internet research projects investigated their use for networking purposes.
What security techniques were important?
Multi-User Operating Systems
In the pre-Web era, computers were large and expensive, and were usually shared by multiple users.
As a result, methods to keep users and their data protected from one another within such systems were
important, and Government contracts supported extensive research and development in this area. The
Multics
time-sharing system was an important example, and served as a precursor to the smaller Unix and Linux systems
that are widely used to this day. The US National Security Agency (NSA)'s
National Computer Security Center (NCSC) created the Trusted Computer System Evaluation Criteria (TCSEC, more
commonly known as the "Orange Book"), which specified system requirements ranging up to levels intended for
use with classified military data.
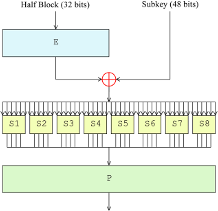
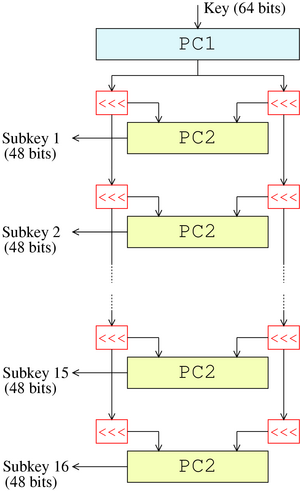
Data Encryption Standard (DES)
The Data Encryption Standard was
developed during the 1970s and standardized by
the U.S. National Bureau of Standards in 1977 as Federal Information Processing Standard (FIPS) 46, and
provided the first widely-used method for computer-based encryption. It was a symmetric algorithm,
encrypting and decrypting 64-bit data blocks with 56-bit keys, performing steps
including those shown in the attached
diagram. Given
the speed of computers at the time, special hardware was often needed to run DES with sufficient performance.
Public-Key Cryptography and the RSA Algorithm
With public-key cryptography, keys are used in pairs, where one member of a pair (the public key)
is used to encrypt messages or check their signatures, and the other member (the private key) is used to decrypt or sign
messages. In most usage, public keys can be circulated freely, while private keys are carefully protected. Public-key
algorithms are usually applied in combination with symmetric algorithms, helping to manage trust between parties in
an effective manner. In 1977, MIT professors Rivest, Shamir, and Adleman published
RSA, the first practical public-key encryption algorithm.
Kerberos
The Kerberos authentication system, developed
in the late 1980s at MIT's Project Athena, authenticates
users to services using symmetric cryptography and an authentication server. Kerberos technology
is still used today, particularly in Microsoft domains.
Privacy-Enhanced Mail (PEM) and early Public-Key Infrastructure (PKI)
Email was a primary application of early interest within and beyond the Internet, and motivated early interest in
security. The Privacy-Enhanced Mail (PEM) project,
initiated in the 1980s, prototyped methods for email encryption
and provided a pilot example for use of public-key certificates and an associated Public-Key Infrastructure (PKI)
in the Internet context. It provided a proof of concept for the subsequent
Secure/Multipurpose Internet Mail Extensions (S/MIME) messaging security protocols, which
have been widely implemented in email clients though have been less widely used.
 Information Security History: A Virtual Overview
Information Security History: A Virtual Overview